Last Update 18 hours ago Total Questions : 49
The NSE5_FCT-7.0 NSE 5 - FortiClient EMS 7.0 content is now fully updated, with all current exam questions added 18 hours ago. Deciding to include NSE5_FCT-7.0 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSE5_FCT-7.0 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSE5_FCT-7.0 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any NSE5_FCT-7.0 NSE 5 - FortiClient EMS 7.0 practice test comfortably within the allotted time.
Refer to the exhibit.
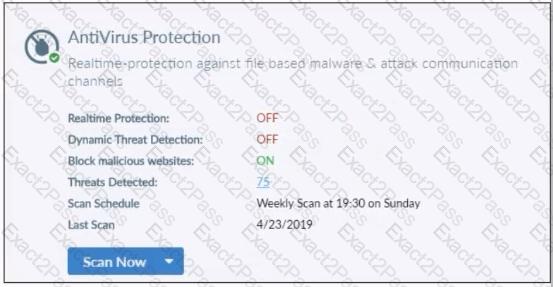
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
Refer to the exhibit.
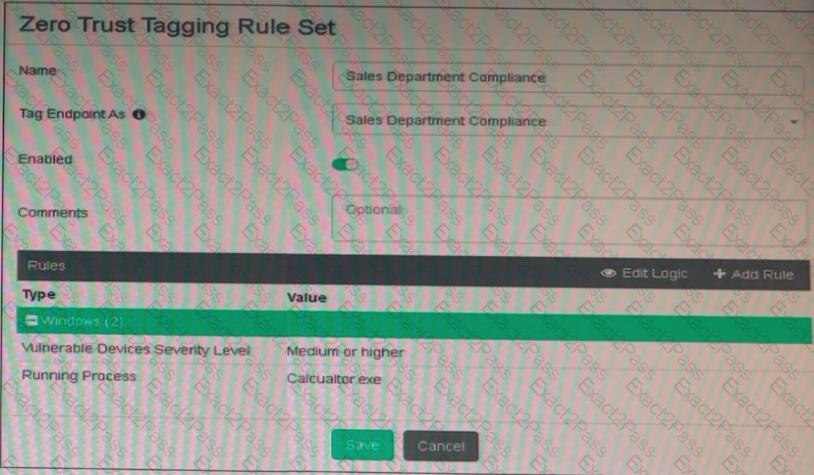
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two.)
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.
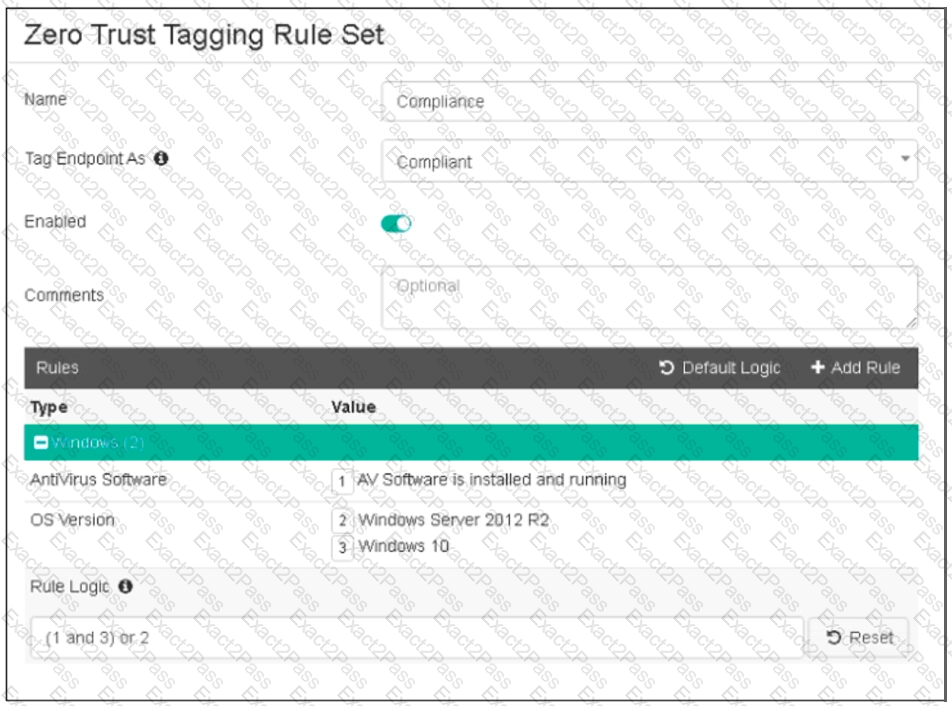
Which two statements about the rule set are true? (Choose two.)
Which three features does FortiClient endpoint security include? (Choose three.)
An administrator configures ZTNA configuration on the FortiGate for remote users. Which statement is true about the firewall policy?
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution"?
Refer to the exhibit.
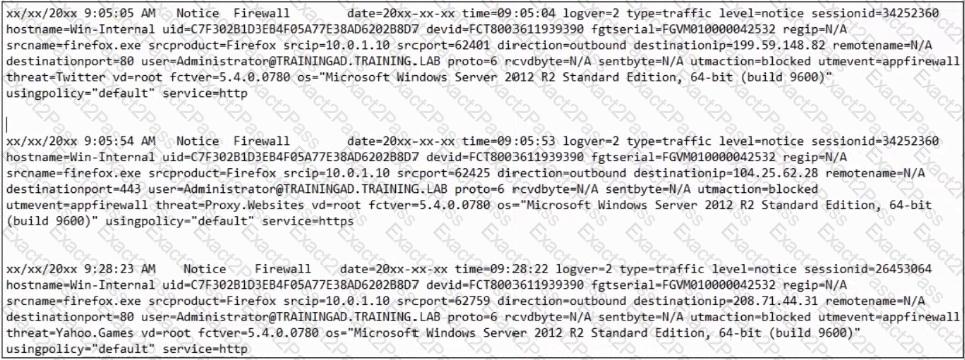
Based on the FortiClient logs shown in the exhibit which application is blocked by the application firewall?

