Last Update 4 hours ago Total Questions : 547
The Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) content is now fully updated, with all current exam questions added 4 hours ago. Deciding to include 350-501 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 350-501 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 350-501 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing and Operating Cisco Service Provider Network Core Technologies (350-501 SPCOR) practice test comfortably within the allotted time.
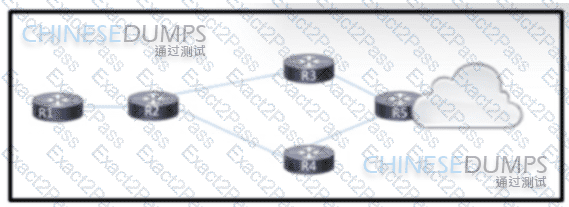
Refer to the exhibit. An engineer is scripting ACLs to handle traffic on the given network. The engineer must block users on the network between R1 and R2 from leaving the network through R5. but these users must still be able to access all resources within the administrative domain. How must the engineer implement the ACL configuration?
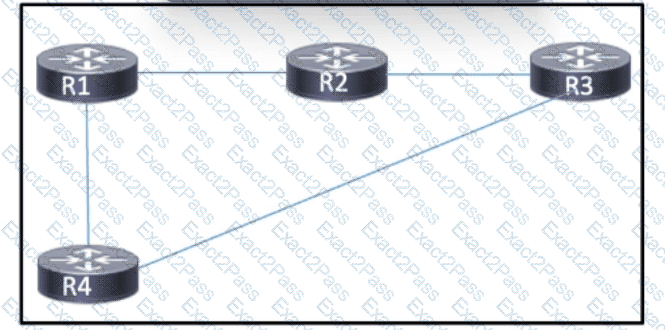
Refer to the exhibit. MPLS is configured within the network. The routers use OSPF to exchange routing information. Hosts that are connected to routers R1 and R3 use routers R2 and R4 to access servers that run a variety of intranet applications. A network engineer must ensure that R1 and R3 maintain an LDP session between them to support the flow of traffic between hosts and servers in case of failure on the path between R1 and R3. Which task should the engineer perform to provide LDP bindings in case of failure on the path between R1 and R3?
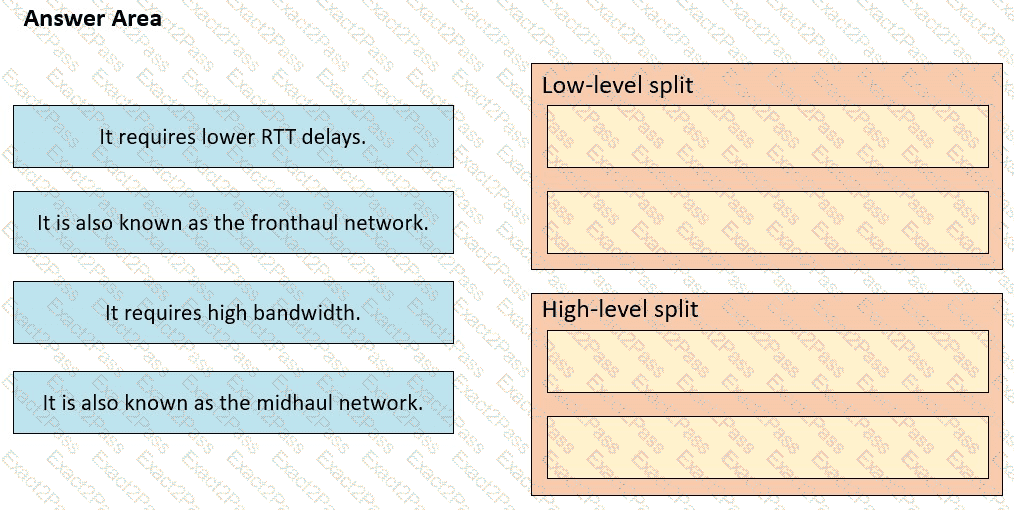
Drag and drop the characteristics from the left onto the corresponding radio splitting approaches on the right
Guidelines -
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology:

Tasks -
Configure the BGP routing protocol for R1 and R2 according to the topology to achieve these goals:
1. Configure EBGP neighbor adjacency for the IPv4 and IPv6 address family between R1 and R2 using Loopback0 IPv4 and IPv6 addresses. All BGP updates must come from the Loopback0 interface as the source. Do not use IGP routing protocols to complete this task.
2. Configure MD5 Authentication for the EBGP adjacency between R1 and R2. The password is clear text C1sc0!.
While an engineer deploys a new Cisco device to redistribute routes from OSPF to BGP, they notice that not all OSPF routes are getting advertised into BGP. Which action must the engineer perform so that the device allows O, OIA, OE1, and OE2 OSPF routes into other protocols?
Refer to the exhibit:
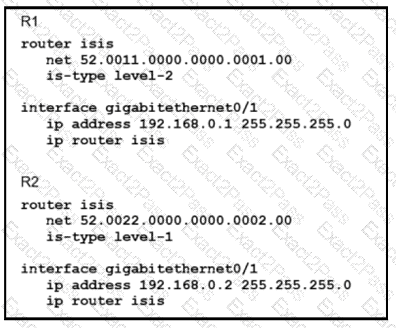
Which statement about the status of the neighbor relationship between R1 and R2 is true?
Which feature describes the weight parameter for BGP path selection?
Refer to the exhibit.

What reestablishes the OSPF neighbor relationship between Router 1 and Router 2?
Refer to the exhibit.

A network operator needs to shut down interface Gi0/0/0/2 for maintenance. What occurs to the interface states of Gi0/0/0/0 and Gi0/0/0/1?
Refer to the exhibit: 
BGPsec is implemented on R1. R2. R3. and R4 BGP peering is established between neighboring autonomous systems Which statement about implementation is true?
What is the primary role of a BR router in a 6rd environment?
Which protocol is used for communication between the PCE and PCC?

