Last Update 22 hours ago Total Questions : 762
The CompTIA Security+ Exam 2025 content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include SY0-701 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our SY0-701 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these SY0-701 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CompTIA Security+ Exam 2025 practice test comfortably within the allotted time.
Which of the following will harden access to a new database system? (Select two)
Which of the following would most likely be used by attackers to perform credential harvesting?
A company wants to track modifications to the code used to build new virtual servers. Which of the following will the company most likely deploy?
A company installed cameras and added signs to alert visitors that they are being recorded. Which of the following controls did the company implement? (Select two).
An IT security team is concerned about the confidentiality of documents left unattended in MFPs. Which of the following should the security team do to mitigate the situation?
A security administrator recently reset local passwords and the following values were recorded in the system:
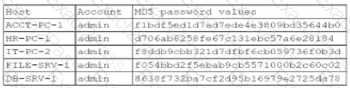
Which of the following in the security administrator most likely protecting against?
A company is concerned with supply chain compromise of new servers and wants to limit this risk. Which of the following should the company review first?
An MSSP manages firewalls for hundreds of clients. Which of the following tools would be most helpful to create a standard configuration template in order to improve the efficiency of firewall changes?
A company asks a vendor to help its internal red team with a penetration test without providing too much detail about the infrastructure. Which of the following penetration testing methods does this scenario describe?
Which of the following is the best way to prevent data from being leaked from a secure network that does not need to communicate externally?
Which of the following is a preventive physical security control?
Which of the following methods would most likely be used to identify legacy systems?

