Last Update 3 hours ago Total Questions : 476
The Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) content is now fully updated, with all current exam questions added 3 hours ago. Deciding to include 200-201 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 200-201 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 200-201 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) practice test comfortably within the allotted time.
Refer to the exhibit.
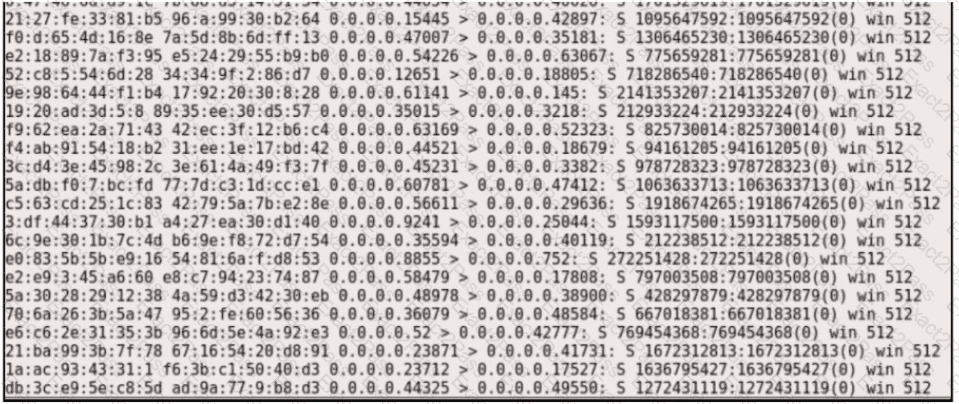
Which type of attack is represented?
Which statement describes indicators of attack?
How does an attacker observe network traffic exchanged between two users?
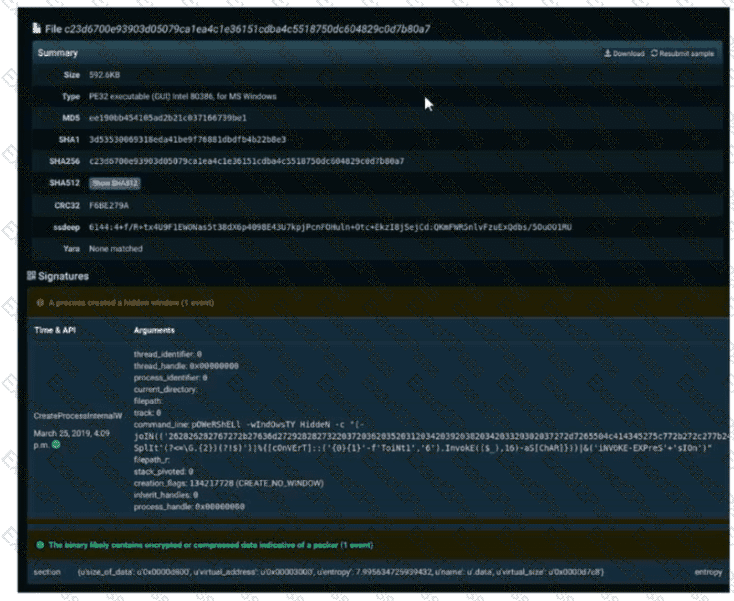
Refer to the exhibit. A SOC engineer is analyzing Cuckoo Sandbox report for a file that has been identified as suspicious by the endpoint security system. What is the state of the file?
Exhibit.
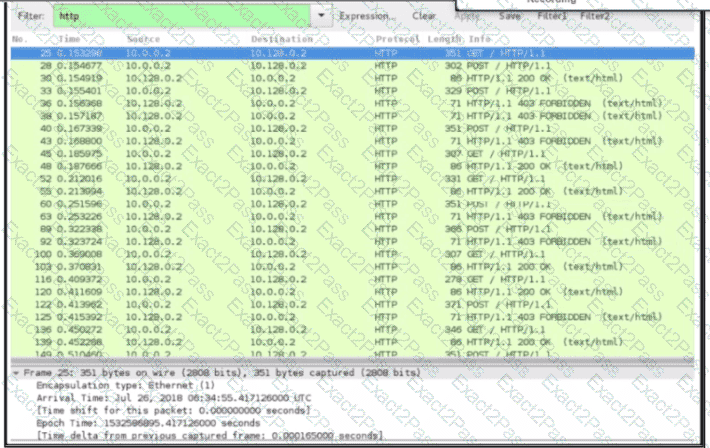
An engineer received a ticket about a slowdown of a web application, Drug analysis of traffic, the engineer suspects a possible attack on a web server. How should the engineer interpret the Wiresharat traffic capture?
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
Refer to the exhibit.

An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?

