Last Update 22 hours ago Total Questions : 339
The Designing Cisco Enterprise Networks (ENSLD) content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include 300-420 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 300-420 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 300-420 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Designing Cisco Enterprise Networks (ENSLD) practice test comfortably within the allotted time.
In Cisco SD-Access. virtual networks create segmentation that allows for separation of users and resources. How is this type of segmentation described?
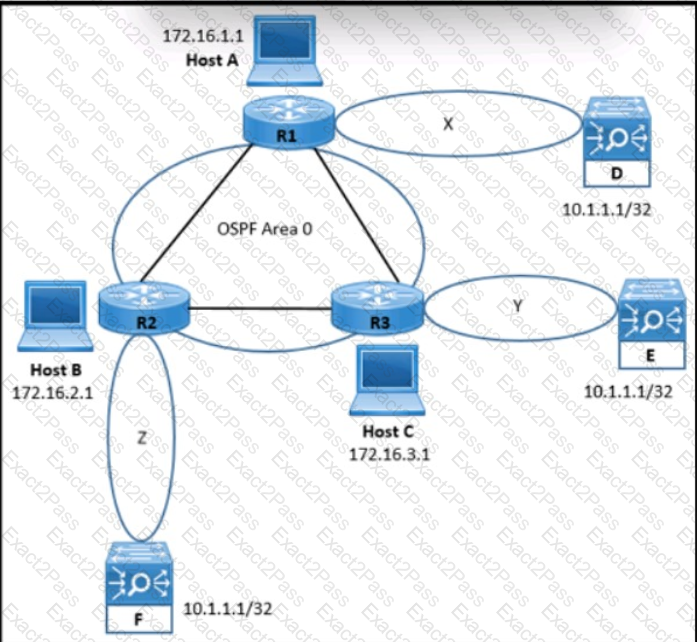
Refer to the exhibit. An engineer is designing an OSPF solution for a customer. The design must take into consideration:
Application load balancers D. E. and F are in different geographical locations and are OSPF-enabled.
Hosts A, B. and C connect to an application through the load balancers using IP address 10.1.1.1/32.
In the event of a failure of one of the load balancers, hosts must still have access to the application.
Which solution must the engineer choose?
A company is planning to open two new branches and allocate the 2a01:c30:16:7009::3800/118 IPv6 network for the region. Each branch should have the capacity to accommodate maximum of 200 hosts. Which two networks should the company use? (Choose two.)
A)

B)

C)

D)

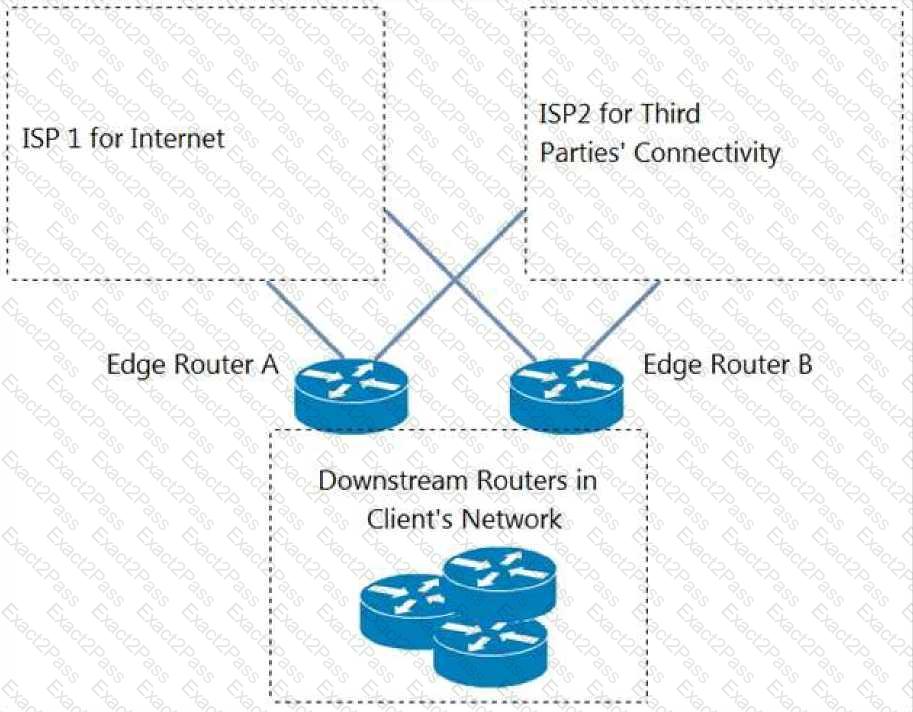
Refer to the exhibit. An engineer is designing a BGP solution for a client that peers with ISP1 for full Internet connectivity and with ISP2 for direct exchange of routes for several third parties. Which action, when implemented on the edge routers, enables the client network to reach the Internet through ISP1?
A company wants to switch from static routing to a dynamic routing protocol to ease the administrative and operational overhead. The network topology is hub and spoke, and the branches use DM VPN back to the hub with two 10-Mbps internet connections. The branch routers are multivendor and have limited memory and CPU resources. Which routing protocol and design solution meets the requirements?
What is the function of the multicast Reverse Path Forwarding check?

