Last Update 6 hours ago Total Questions : 726
The Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) content is now fully updated, with all current exam questions added 6 hours ago. Deciding to include 350-701 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 350-701 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 350-701 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) practice test comfortably within the allotted time.
Refer to the exhibit.
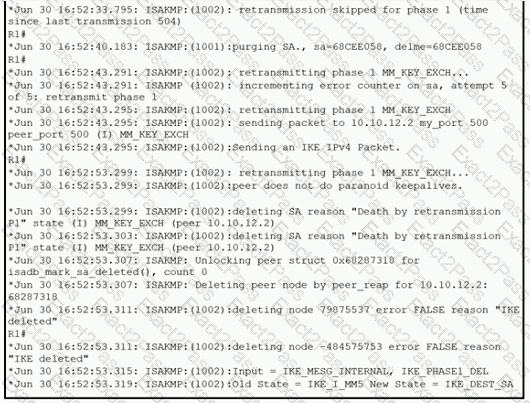
A network administrator configured a site-to-site VPN tunnel between two Cisco IOS routers, and hosts are unable to communicate between two sites of VPN. The network administrator runs the debug crypto isakmp sa command to track VPN status. What is the problem according to this command output?
What is a difference between weak passwords and missing encryption?
An engineer is configuring cloud logging using a company-managed Amazon S3 bucket for Cisco Umbrella logs. What benefit does this configuration provide for accessing log data?
Which API method and required attribute are used to add a device into Cisco DNA Center with the native API?
Which role is a default guest type in Cisco ISE?
Refer to the exhibit.
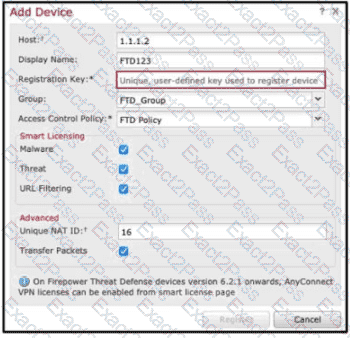
An administrator is adding a new Cisco FTD device to their network and wants to manage it with Cisco FMC.
The Cisco FTD is not behind a NAT device. Which command is needed to enable this on the Cisco FTD?
Which problem Is solved by deploying a multicontext firewall?
An engineer is configuring their router to send NetfFow data to Stealthwatch which has an IP address of 1 1 11 using the flow record Stea!thwatch406397954 command Which additional command is required to complete the flow record?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites
but other sites are not accessible due to an error. Why is the error occurring?
In an IaaS cloud services model, which security function is the provider responsible for managing?
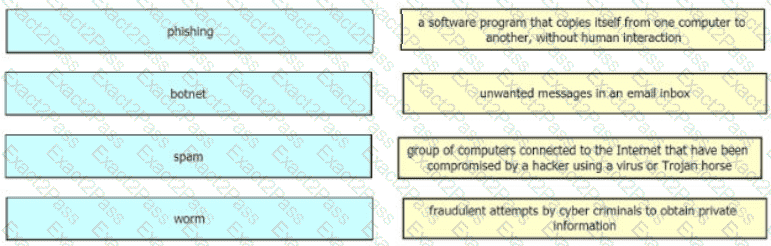
Drag and drop the common security threats from the left onto the definitions on the right.
An engineer is configuring Cisco WSA and needs to deploy it in transparent mode. Which configuration component must be used to accomplish this goal?

